Comparison Study on VPN and I2P
I2P or invisible internet project is a sort of internet browsing network. It helps people to send files and encrypted messages anonymously. The original IP address of the sender of the data is not recognizable or traceable. It increases the degree of data safekeeping/security.
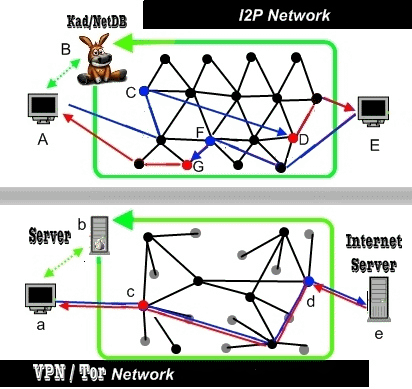
I2P and VPN –Both Capable of Maintaining Privacy to Send Data
However, like I2P, the independent VPN/ virtual private network system is digitally upgraded to transfer data. It also keeps IP address of the internet user secret. Both hi-tech servers enable people to do file sharingunder the pseudonyms. These two private servers provide the guarantee for better data protection and the full fledged privacy.
Focus on Data Security While Installing VPN and I2P
However while evaluating respective roles of I2P and VPN, you will have to focus on the importance of security/confidentiality to deliver data. Invisible internet project software is easy to install whereas VPN tool installation is not much easier. Good tech support is needed to run VPN.
I2P with Different Data Transfer Modes
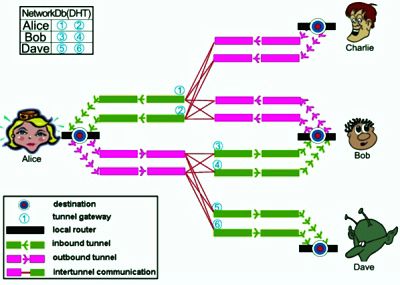 Invisible internet project or I2P interface is a different mod of data transfer through multiple nodes. Devices which are used to run I2P are called nodes. So, hackers don’t find the original source of IP port.
Invisible internet project or I2P interface is a different mod of data transfer through multiple nodes. Devices which are used to run I2P are called nodes. So, hackers don’t find the original source of IP port.
In practical field, data which travels through I2P interface require multiple computers with I2P ports. Therefore data hackers get different fake IP addresses. So the anonymity is well kept when you use this type of invisible internet project for data conversion. Your internet connection will be totally separated from the real broadband. It is a private tele-communication system.
I2P users have several automatic data switching modes to divert the routes of data supply. Therefore, it is very difficult for outsiders to decode the real.
VPN – More Powerful to Maintain Anonymity
IP addresses of I2P tools. However, some critics claim that there are many advanced IP decoders which are useful to unlock I2P ports. Slowly, hackers discover the data access routes to enter into I2P. The same fear is palpable in the case of installing Chrome and Java Script. To be frank, VPN is the right software to control the data hacking.
A virtual private networking system is also competent to camouflage the i2p connectivity if you shoot data via VPN to I2P. So, if you need higher anonymity and data security, install VPN tool for usage.
On the other hand, VPN service is not cost effective. It relies on the rental packages provided by various VPN companies. If you have a small start-up company, kindly choose other virtual private data transfer networks like Tor. VPN is suitable to large IT firms which have manpower and money to maintain this powerful data management infrastructure. Finally, before installation of VPN or I2P, talk to technical experts to select the best internet browsing platform.










No Comments